Agent Tesla – Basic Analysis
Agent Tesla
A remote access trojan capable of gathering sensitive data from an infected machine, including login credentials, system details, banking information, and various personal data.
The analysis below leverages on ANY.RUN which makes behavioral analysis much easier.
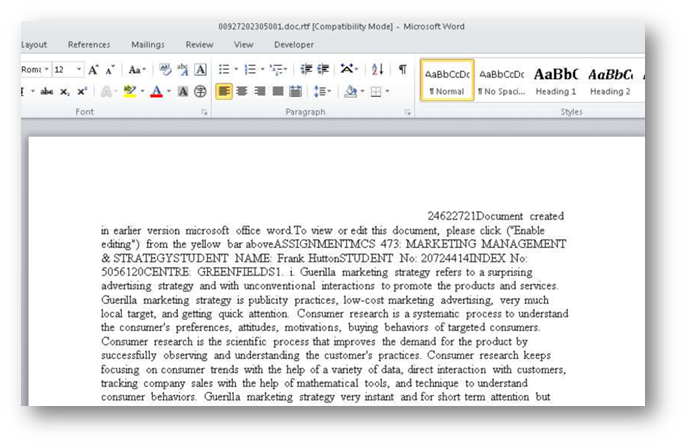
File Name: 00927202305001.doc
File Size: 44.21 kb
SHA256: 6aefe0bd42c68c1a2a4294c7923939ce5f68f892a21f1606772561b6c7037ce6
Reference: hxxps://app.any.run/tasks/9ca83159-55d8-48d8-8e8c-a5e69a31edd2/
C2 Server: ftp[DOT]valvulasthermovalve[DOT]cl
Behavioral Triggers:
- Malicious file contains an embedded payload to exploit CVE-2017-11882 (MS Office RCE – Memory Corruption) –
MITRE Execution T1203 – Exploitation for client execution
Suricata Rule Trigger – ET DROP Spamhaus DROP Listed Traffic Inbound group 39
- MITRE Discovery T1012 – Query Registry
Reads the Internet Settings – HKEY_CURRENT_USER\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- MITRE Discovery T1082 – System Information Discovery
Checks proxy server information
Checks supported languages
Reads the computer name
Reads the machine GUID from the registry
Reads Environment values
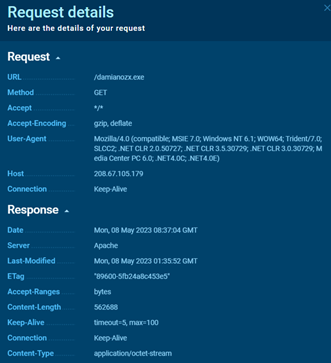
- Malware (damianozx.exe) was downloaded from 208.67.105[DOT]179 – MITRE Command-and-Control T1105 – Ingress Tool Transfer
Suricata Rule Trigger – ET INFO Executable Download from dotted-quad Host
Suricata Rule Trigger – ET MALWARE Likely Evil EXE download from dotted Quad by MSXMLHTTP M1
Suricata Rule Trigger – ET MALWARE Likely Evil EXE download from dotted Quad by MSXMLHTTP M2
Suricata Rule Trigger – ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response
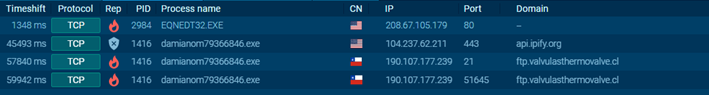
- Malware damianozx.exe executes itself
MITRE Discovery T1582 – Software Discovery – Malware enumerated software installations
MITRE Credential Access T1555.003 – Credentials from Password Stores
MITRE Credential Access T1552.001 – Credentials in Files
MITRE Collection T1114.001 – Email Collection – Local Email Collection
MITRE Command-and-Control T1571 – Non-standard port – Connection on port 51645
MITRE Command-and-Control T1071 – FTP – Connects to FTP
Suricata Rule Trigger – ET MALWARE AgentTesla Exfil via FTP
YARA detections:
Rule name: SUSP_INDICATOR_RTF_MalVer_Object
Description: Detects RTF documents with non-standard version and embedding one of the objects mostly observed in exploit (e.g. CVE-2017-11882) documents.
Reference: https://github.com/ditekshen/detection
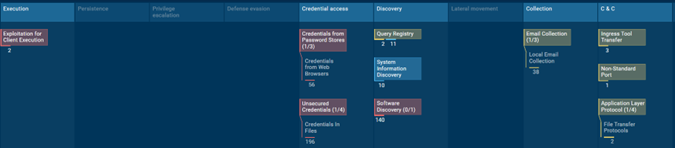
MITRE Matrix:
MITRE Execution T1203 – Exploitation for client execution
MITRE Discovery T1012 – Query Registry
MITRE Discovery T1082 – System Information Discovery
MITRE Discovery T1582 – Software Discovery – Malware enumerated software installations
MITRE Credential Access T1555.003 – Credentials from Password Stores
MITRE Credential Access T1552.001 – Credentials in Files
MITRE Collection T1114.001 – Email Collection – Local Email Collection
MITRE Command-and-Control T1105 – Ingress Tool Transfer
MITRE Command-and-Control T1571 – Non-standard port – Connection on port 51645
MITRE Command-and-Control T1071.002 – Application Layer Protocol – FTP – Connects to FTP