Lokibot – Basic Analysis
Lokibot
An information-stealing malware designed to extract data from the machines of its victims, including stored account credentials, banking details, and other personal information.
The analysis below leverages on ANY.RUN which makes behavioral analysis much easier.
File Name: 443a8b589b828915caf8.dll
File Size: 130400 bytes
SHA256: 8c5982fded8fe30254f51d439888fa007ef83f4067c212e343d007530f278759
C2 Server: hxxp://208.67.105.148/web/five/fre.php
Behavioral Triggers:
- Attempts to connect to an IP address – 208[.]67.105.148:80
- Enumerates running processes.
- Creates RWX Memory – API VirtualProtectEx – modification to allow write or execution
- Terminates another process – API NtTerminateProcess – possibly tried to terminate AV program
- Steals information from installed browser:
file: C:\Users\Louise\AppData\Roaming\Mozilla\Firefox\Profiles\0f9yudun.default\key4.db
file: C:\Users\Louise\AppData\Roaming\Mozilla\Firefox\Profiles\0f9yudun.default\cert9.db
file: C:\Users\Louise\AppData\Roaming\Mozilla\Firefox\Profiles\0f9yudun.default\logins.json
file: C:\Users\Louise\AppData\Roaming\Mozilla\Firefox\profiles.ini
- Spoofs its process to act as a child process of a legitimate one: rundll32.exe – API CreateProcessInternalW
- Credential harvest for FTP Client software:
file: C:\Users\Louise\AppData\Roaming\FileZilla\sitemanager.xml
file: C:\Users\Louise\AppData\Roaming\FileZilla\recentservers.xml
file: C:\Users\Louise\AppData\Roaming\Far Manager\Profile\PluginsData\42E4AEB1-A230-44F4-B33C-F195BB654931.db
file: C:\Program Files (x86)\FTPGetter\Profile\servers.xml
file: C:\Users\Louise\AppData\Roaming\FTPGetter\servers.xml
file: C:\Users\Louise\AppData\Roaming\Estsoft\ALFTP\ESTdb2.dat
regkey: HKEY_CURRENT_USER\Software\Far2\Plugins\FTP\Hosts
regkey: HKEY_CURRENT_USER\Software\Far\Plugins\FTP\Hosts
regkey: HKEY_CURRENT_USER\Software\Ghisler\Total Commander
regkey: HKEY_CURRENT_USER\Software\LinasFTP\Site Manager
- Credential harvest for instant messaging client:
file: C:\Users\Louise\AppData\Roaming\.purple\accounts.xml – Used by Pidgin
- Credential harvest for email clients:
file: C:\Users\Louise\AppData\Roaming\Thunderbird\profiles.ini
regkey: HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook
regkey: HKEY_CURRENT_USER\Software\Microsoft\Office\15.0\Outlook\Profiles\Outlook
regkey: HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Outlook\Profiles\Outlook
- Collects system information:
regkey: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\MachineGuid
YARA detections:
Hit: PID 1064 trigged the Yara rule ‘HeavensGate’
Hit: PID 1064 trigged the Yara rule ‘LokiBot’
Hit: PID 1336 trigged the Yara rule ‘shellcode_stack_strings’
Hit: PID 1336 trigged the Yara rule ‘HeavensGate’
Hit: PID 1336 trigged the Yara rule ‘LokiBot’
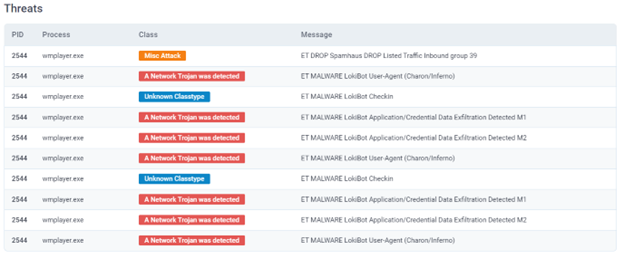
Suricata Detections:
References: hXXps://app.any.run/tasks/0786c679-560a-43bf-aba7-4ac7e9571f44/
hXXps://bazaar.abuse.ch/sample/8c5982fded8fe30254f51d439888fa007ef83f4067c212e343d007530f278759/#yara
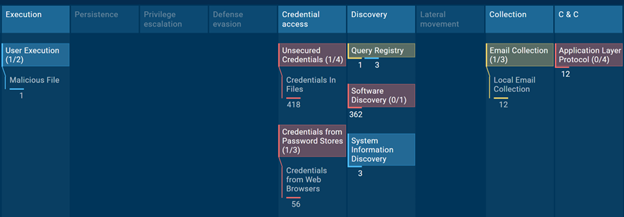
MITRE Matrix
Execution – T1204.002 User Execution: Malicious File
Credential Access –
T1552.001 Unsecured Credentials: Credentials in Files
T1555.003 Credentials from password stores: Credentials from web browsers
Discovery –
T1012 Query Registry
T1518 Software Discovery
T1082 Software Information Discovery
Collection –
T1114.001 Local Email Collection
Command-and-Control –
T1071 Application Layer Protocol